Guide setup Configure a web application firewall (WAF) for App Service
A web application firewall (WAF) protects web applications from a variety of application layer attacks such as cross-site scripting (XSS), SQL injection, and cookie poisoning, among others. Attacks to apps are the leading cause of breaches—they are the gateway to your valuable data. With the right WAF in place, you can block the array of attacks that aim to exfiltrate that data by compromising your systems.
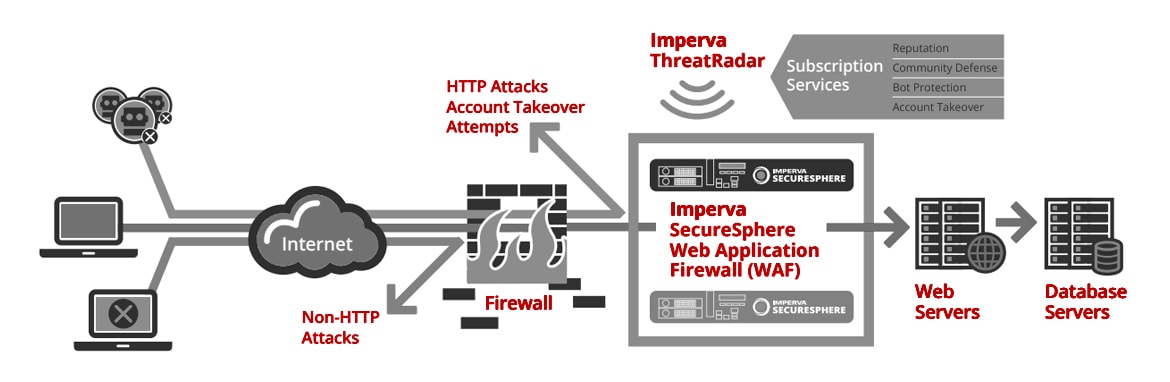
How does a web application firewall (WAF) work?
A WAF protects your web apps by filtering, monitoring, and blocking any malicious HTTP/S traffic traveling to the web application, and prevents any unauthorized data from leaving the app. It does this by adhering to a set of policies that help determine what traffic is malicious and what traffic is safe. Just as a proxy server acts as an intermediary to protect the identity of a client, a WAF operates in similar fashion but in the reverse—called a reverse proxy—acting as an intermediary that protects the web app server from a potentially malicious client.
WAFs can come in the form of software, an appliance, or delivered as-a-service. Policies can be customized to meet the unique needs of your web application or set of web applications. Although many WAFs require you update the policies regularly to address new vulnerabilities, advances in machine learning enable some WAFs to update automatically. This automation is becoming more critical as the threat landscape continues to grow in complexity and ambiguity.
The difference between a web application firewall (WAF), an intrusion prevention system (IPS) and a next-generation firewall (NGFW)
An IPS is an intrusion prevention system, a WAF is a web application firewall, and an NGFW is a next-generation firewall. What’s the difference between them all?
An IPS is a more broadly focused security product. It is typically signature and policy based—meaning it can check for well-known vulnerabilities and attack vectors based on a signature database and established policies. The IPS establishes a standard based off the database and policies, then sends alerts when any traffic deviates from the standard. The signatures and policies grow over time as new vulnerabilities are known. In general, IPS protects traffic across a range of protocol types such as DNS, SMTP, TELNET, RDP, SSH, and FTP. IPS typically operates and protects layers 3 and 4. The network and session layers although some may offer limited protection at the application layer (layer 7).
A web application firewall (WAF) protects the application layer and is specifically designed to analyze each HTTP/S request at the application layer. It is typically user, session, and application aware, cognizant of the web apps behind it and what services they offer. Because of this, you can think of a WAF as the intermediary between the user and the app itself, analyzing all communications before they reach the app or the user. Traditional WAFs ensure only allowed actions (based on security policy) can be performed. For many organizations, WAFs are a trusted, first line of defense for applications, especially to protect against the OWASP Top 10—the foundational list of the most seen application vulnerabilities. This Top 10 currently includes:
Injection attacks
Broken Authentication
Sensitive data exposure
XML External Entities (XXE)
Broken Access control
Security misconfigurations
Cross Site Scripting (XSS)
Insecure Deserialization
Get the Ebook on how to be prepared for the OWASP top 10
Watch this short video on IPS vs WAF
A next-generation firewall (NGFW) monitors the traffic going out to the Internet—across web sites, email accounts, and SaaS. Simply put, it’s protecting the user (vs the web application). A NGFW will enforce user-based policies and adds context to security policies in addition to adding features such as URL filtering, anti-virus/anti-malware, and potentially its own intrusion prevention systems (IPS). While a WAF is typically a reverse proxy (used by servers), NGFWs are often forward proxys (used by clients such as a browser).
The different ways to deploy a WAF
A WAF can be deployed in several ways—it all depends on where your applications are deployed, the services needed, how you want to manage it, and the level of architectural flexibility and performance you require. Do you want to manage it yourself, or do you want to outsource that management? Is it a better model to have a cloud-based, option or do you want your WAF to sit on-premises? How you want to deploy will help determine what WAF is right for you. Below are your options.
WAF Deployment Modes:
Cloud-based + Fully Managed as a Service—this is a great option if you require the fastest, most hassle-free way to get WAF in front of your apps (especially if you have limited in-house security/IT resources)
Cloud-based + Self Managed—get all the flexibility and security policy portability of the cloud while still retaining control of traffic management and security policy settings
Cloud-based + Auto-Provisioned—this is the easiest way to get started with a WAF in the cloud, deploying security policy in an easy, cost-effective way
On-premises Advanced WAF (virtual or hardware appliance)—this meets the most demanding deployment requires where flexibility, performance and more advanced security concerns are mission critical
Here’s a guide to help you choose which WAF and deployment mode is right for you.
Learn more about WAF and how to protect your apps with F5 's Advanced WAF technology
Searches related to how to setup a web application firewall
web application firewall azure
how to disable web application firewall
web application firewall architecture
web application firewall tutorial
web application firewall youtube
web application firewall vendors
aws waf
python web application firewall
- What is a Web Application Firewall (WAF) difference between blacklist and whitelist?
- News Cloud Storage Backup Data VPS | What’s new at Vultr?
- What is a cloud server and how does it work? Create your Cloud Backup business?
- Review service Products and pricing Platform Google Cloud Storage
- Review introduce service AWS amazon.com Product and Technical
Operate and exploit advertising by iCOMM Vietnam Media and Technology Joint Stock Company.
Adress: 99 Nguyen Tat Thanh, To 2, Khu 6, Thi tran Tan Phu, Tan Phu, Dong Nai.
Email: phuongtran2191@gmail.com | Tel: (+84) 984654960
Editor in chief: Tran Nha Phuong
Company: Lucie Guillot (Nha Phuong Tran)




